System Logs: 7 Powerful Insights Every IT Pro Must Know
System logs are the silent witnesses of every digital operation, quietly recording events that can make or break your IT infrastructure. Understanding them isn’t just technical—it’s essential for security, performance, and compliance.
What Are System Logs and Why They Matter

At the heart of every operating system, application, and network device lies a continuous stream of recorded events known as system logs. These logs capture everything from user logins and file access to hardware failures and software errors. They serve as a digital diary, offering a chronological record of activities that occur within a computing environment.
The Definition and Core Purpose of System Logs
System logs are structured or unstructured text files generated by operating systems, applications, and network devices to document events. Their primary purpose is to provide visibility into system behavior, enabling administrators to monitor health, troubleshoot issues, and ensure security.
- They record timestamps, event types, user IDs, IP addresses, and error codes.
- Logs help in diagnosing boot failures, application crashes, and unauthorized access attempts.
- They are foundational for audit trails in regulated industries like finance and healthcare.
“Without system logs, troubleshooting is like navigating in the dark—possible, but dangerously inefficient.” — IT Operations Expert, Jane Rivera
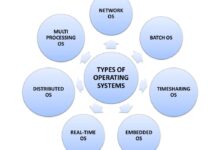
Types of System Logs Across Platforms
Different operating systems and environments generate distinct types of system logs. Understanding these variations is crucial for effective monitoring and analysis.
Windows Event Logs: Divided into Application, Security, and System logs, managed via Event Viewer.These logs use structured XML format and are critical for Active Directory and domain-level monitoring.Microsoft’s official documentation details how these logs are structured and accessed.Linux Syslog: Traditionally stored in /var/log/, including files like syslog, auth.log, and kernel.log.Modern systems use journald via systemd, offering binary logging with rich metadata.
.macOS Unified Logging: Introduced in macOS Sierra, it consolidates logs from apps, system processes, and kernel into a single, efficient system accessible via the log command.Network Device Logs: Routers and firewalls (e.g., Cisco, Palo Alto) generate logs for traffic flow, access control, and intrusion detection, often sent to a centralized syslog server.The Critical Role of System Logs in Cybersecurity
In today’s threat landscape, system logs are not just diagnostic tools—they are frontline defense mechanisms.Cyberattacks often leave digital footprints in logs long before they escalate into breaches..
Detecting Unauthorized Access and Intrusions
One of the most vital uses of system logs is identifying suspicious login attempts. Failed SSH logins, repeated password errors, or logins from unusual geographic locations can signal brute-force attacks or credential stuffing.
- Security logs in Windows track event IDs like 4625 (failed login) and 4670 (permissions change).
- Linux
auth.logrecords SSH attempts, sudo usage, and PAM authentication events. - Tools like OSSEC and Elastic SIEM use these logs to trigger real-time alerts.
Forensic Analysis After a Security Breach
When a breach occurs, system logs become the primary source for digital forensics. Investigators use logs to reconstruct the attack timeline, identify compromised accounts, and determine the scope of data exfiltration.
- Logs can reveal lateral movement across networks, such as unexpected RDP connections or PowerShell executions.
- Timestamp correlation across multiple systems helps establish the sequence of events.
- Regulatory frameworks like GDPR and HIPAA require log retention for forensic readiness.
“The difference between a contained incident and a catastrophic breach often lies in the quality and availability of system logs.” — Cybersecurity Analyst, Mark Teller
How System Logs Enhance System Performance Monitoring
Beyond security, system logs are indispensable for maintaining optimal performance. They provide early warnings of resource exhaustion, software bugs, and configuration drift.
Identifying Performance Bottlenecks
Logs from system daemons, databases, and web servers often contain clues about performance degradation. For example:
- Apache or Nginx error logs showing
502 Bad Gatewayor504 Gateway Timeoutindicate backend service failures. - Database logs (e.g., MySQL’s
error.log) may reveal slow queries or connection pool exhaustion. - Windows Performance Monitor can correlate event logs with CPU, memory, and disk usage metrics.
By parsing these logs, administrators can proactively scale resources or optimize queries before users are impacted.
Proactive Maintenance Using Log Trends
Regular analysis of system logs enables predictive maintenance. For instance:
- Recurring disk full errors (
event ID 2013in Windows) suggest the need for automated cleanup scripts. - Frequent service restarts logged in
systemdjournal may indicate memory leaks or misconfigurations. - Log aggregation tools like Graylog or Splunk can visualize trends over time, helping teams spot anomalies before they become outages.
Best Practices for Managing System Logs
Poor log management can render even the most detailed logs useless. Implementing best practices ensures logs are reliable, secure, and actionable.
Centralized Logging and Log Aggregation
Storing logs on individual machines makes analysis inefficient and risky—if a server crashes, logs may be lost. Centralized logging solves this by forwarding logs to a dedicated server.
- Tools like rsyslog and syslog-ng forward Linux logs to a central server.
- Windows can use Windows Event Forwarding (WEF) or third-party agents to send events to SIEM platforms.
- Cloud environments use services like Amazon CloudWatch or Google Cloud Logging for unified log collection.
Log Rotation and Retention Policies
Uncontrolled log growth can consume disk space and degrade system performance. Log rotation automatically archives and compresses old logs.
- Linux uses
logrotateto manage file size and retention (e.g., keep 30 days of logs). - Windows can configure Event Log properties to limit size and overwrite old entries.
- Compliance standards often dictate retention periods—e.g., PCI DSS requires 1 year of logs, with 3 months immediately available.
Tools and Technologies for Analyzing System Logs
Manual log inspection is impractical in large environments. Modern tools automate parsing, correlation, and alerting.
Open-Source Log Management Solutions
Several powerful open-source tools help organizations analyze system logs without high licensing costs.
- ELK Stack (Elasticsearch, Logstash, Kibana): A popular trio for ingesting, indexing, and visualizing logs. Elastic’s documentation provides extensive setup guides.
- Graylog: Offers a user-friendly interface, alerting, and stream-based log routing.
- Fluentd: A data collector that unifies log forwarding from various sources.
Commercial SIEM and Log Analytics Platforms
For enterprises, commercial tools offer advanced features like AI-driven anomaly detection and compliance reporting.
- Splunk: Known for its powerful search language (SPL) and real-time dashboards.
- IBM QRadar: Integrates network flow data with system logs for comprehensive threat detection.
- Microsoft Sentinel: A cloud-native SIEM that leverages Azure for scalable log analysis.
Compliance and Legal Requirements for System Logs
System logs are not just technical artifacts—they are legal documents in many jurisdictions. Regulatory frameworks mandate their collection, protection, and retention.
GDPR, HIPAA, and PCI DSS Compliance
Different industries have specific log-related requirements:
- GDPR: Requires logs to demonstrate accountability and data processing transparency. Access logs must show who accessed personal data and when.
- HIPAA: Mandates audit logs for all systems handling protected health information (PHI), including login attempts and file access.
- PCI DSS: Requires logging of all access to cardholder data, with at least one year of retention and secure storage to prevent tampering.
Ensuring Log Integrity and Non-Repudiation
To meet compliance, logs must be tamper-proof and trustworthy.
- Use secure protocols like TLS when forwarding logs to prevent interception.
- Implement write-once, read-many (WORM) storage or blockchain-based logging for immutability.
- Regularly audit log access controls to prevent insider threats.
“A log that can be altered is no log at all—it’s a liability.” — Compliance Officer, Lena Choi
Common Challenges in System Log Management
Despite their value, managing system logs comes with significant challenges that organizations must overcome.
Log Volume and Noise
Modern systems generate terabytes of logs daily. Much of this data is routine or redundant, making it hard to spot critical events.
- Implement filtering rules to suppress low-severity events (e.g., routine service startups).
- Use machine learning to baseline normal behavior and flag deviations.
- Normalize log formats across systems to improve searchability.
Log Format Inconsistencies
Different vendors and applications use varying log formats—some use JSON, others plain text or syslog RFC 3164/5424.
- Use log parsers (e.g., Grok patterns in Logstash) to extract structured fields.
- Adopt standardized formats like CEF (Common Event Format) or LEEF for interoperability.
- Document log schemas for internal applications to ensure consistency.
Future Trends in System Logs and Log Analytics
The field of log management is evolving rapidly, driven by cloud adoption, AI, and increasing regulatory demands.
AI and Machine Learning in Log Analysis
AI is transforming log analytics from reactive to predictive. Tools now use ML to detect anomalies, classify events, and reduce false positives.
- Unsupervised learning models identify unusual patterns without predefined rules.
- Natural language processing (NLP) helps parse unstructured log messages for sentiment and intent.
- Vendors like Splunk and Datadog integrate AI-powered anomaly detection into their platforms.
Cloud-Native and Containerized Logging
With the rise of Kubernetes and microservices, traditional logging approaches are insufficient.
- Containers are ephemeral—logs must be collected in real-time before pods disappear.
- Solutions like Fluent Bit and OpenTelemetry provide lightweight agents for container environments.
- Serverless platforms (e.g., AWS Lambda) require integration with cloud logging APIs.
What are system logs used for?
System logs are used for monitoring system health, detecting security threats, troubleshooting technical issues, ensuring regulatory compliance, and conducting forensic investigations after incidents.
How long should system logs be retained?
Retention periods vary by regulation and industry. Generally, 30 to 90 days is standard for operational use, while compliance requirements like PCI DSS mandate up to one year of retention.
Can system logs be tampered with?
Yes, if not properly secured. Logs stored locally can be altered by attackers with administrative access. To prevent tampering, logs should be forwarded to a secure, centralized server with write-once storage and access controls.
What is the best tool for analyzing system logs?
There is no single “best” tool—it depends on needs. For open-source solutions, ELK Stack and Graylog are excellent. For enterprise environments, Splunk, IBM QRadar, or Microsoft Sentinel offer advanced features and scalability.
How do I enable logging on a Linux server?
Most Linux systems have logging enabled by default via rsyslog or systemd-journald. To customize, edit /etc/rsyslog.conf or use journalctl for systemd logs. Ensure log rotation is configured via /etc/logrotate.d/.
System logs are far more than technical footnotes—they are the backbone of modern IT operations. From securing networks to optimizing performance and meeting legal obligations, their role is indispensable. As technology evolves, so too must our approach to collecting, analyzing, and protecting these vital records. By embracing best practices and leveraging powerful tools, organizations can turn raw log data into actionable intelligence, ensuring resilience in an increasingly complex digital world.
Further Reading: