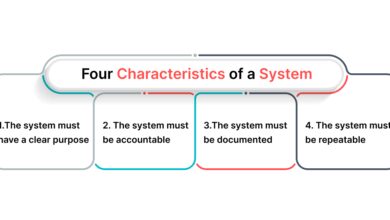
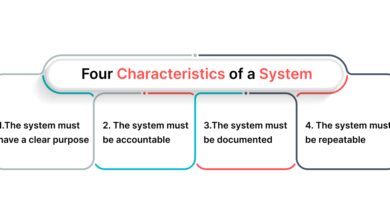
System Group: 7 Powerful Insights You Must Know
In today’s fast-evolving technological landscape, the term system group has become more than just a buzzword—it’s a cornerstone of modern computing, organizational structure, and digital infrastructure. Whether you’re managing IT networks or building enterprise software, understanding what a system group truly entails can unlock efficiency, security, and scalability like never before.
What Is a System Group? A Foundational Overview

The concept of a system group is central to how modern operating systems, network infrastructures, and software platforms manage access, permissions, and resource allocation. At its core, a system group is a logical collection of users, processes, or devices that share common attributes, roles, or access rights within a computing environment. This grouping mechanism simplifies administration and enhances security by allowing policies to be applied collectively rather than individually.
Defining the System Group in Computing
In computing, a system group typically refers to a set of user accounts grouped under a single identifier for administrative convenience. For example, in Unix-like operating systems such as Linux, groups are used to define which users can read, write, or execute specific files and directories. The /etc/group file stores group definitions, and commands like groupadd, usermod, and groups are used to manage them.
- Each user can belong to one or more system groups.
- Groups reduce administrative overhead by enabling bulk permission settings.
- System groups are essential for role-based access control (RBAC).
This model is not limited to local machines; it scales across enterprise environments using directory services like LDAP or Active Directory.
System Group vs. User Group: Understanding the Difference
While the terms may seem interchangeable, there’s a subtle but important distinction between a system group and a general user group. A system group often refers to low-level, system-defined groups critical for OS functionality—such as root, daemon, sys, or adm—which are created during installation and used by system processes.
System groups: Reserved for system-level operations and services.User groups: Created for human users to manage file and resource access.Some systems reserve group IDs below 1000 for system groups to differentiate them from user-created ones..
“System groups are the invisible scaffolding that holds together user permissions and process privileges in multi-user environments.” — Linux Administration Handbook, 5th Edition
The Role of System Groups in Security Management
Security is one of the most critical applications of system groups.By assigning users to specific groups, administrators can enforce the principle of least privilege—ensuring individuals only have access to resources necessary for their role.For instance, members of the sudo group on Debian-based systems can execute commands with elevated privileges, while the docker group allows users to interact with containerized applications without requiring root access..
- Prevents unauthorized access to sensitive system files.
- Enables audit trails through group-based logging.
- Facilitates compliance with standards like ISO 27001 or GDPR by defining clear access boundaries.
Improper group management, however, can lead to privilege escalation vulnerabilities. For example, adding a regular user to the root group (if such a group exists) could compromise the entire system.
System Group in Operating Systems: Linux, Windows, and macOS
Different operating systems implement the concept of a system group in unique ways, reflecting their underlying architecture and design philosophy. While the fundamental goal—efficient access control—remains consistent, the implementation details vary significantly across platforms.
Linux: The Birthplace of Modern System Groups
Linux, derived from Unix, has one of the most mature and transparent implementations of system groups. Every process and file in Linux is associated with an owner and a group, and permissions are defined using a 9-bit model (read, write, execute for owner, group, and others).
- The
idcommand displays a user’s UID, GID, and all supplementary groups. - Primary group membership is defined in
/etc/passwd, while supplementary groups are listed in/etc/group. - Commands like
newgrpallow temporary switching to another group context.
Advanced features like Access Control Lists (ACLs) extend basic group permissions, allowing finer control over who can access what. You can learn more about Linux group management at the GNU Bash Manual.
Windows: Active Directory and Local Security Groups
In Windows environments, especially those integrated with Active Directory (AD), the concept of a system group evolves into security groups and distribution groups. Security groups are used for access control, while distribution groups are typically for email communication.
- Built-in groups like
Administrators,Users, andGuestsdefine default access levels. - Domain-level groups in AD allow centralized management across thousands of machines.
- Group Policy Objects (GPOs) apply configurations based on group membership.
Unlike Linux, Windows uses Security Identifiers (SIDs) instead of numeric GIDs, making group identification more complex but also more flexible in large networks. Microsoft provides comprehensive documentation on group strategies in its Active Directory Security Groups Guide.
macOS: Unix Under the Hood, Apple Design on Top
macOS, being Unix-based, inherits much of Linux’s group management logic but wraps it in a user-friendly interface. System groups in macOS are managed via the Directory Utility or command-line tools like dscl.
- Common system groups include
admin,_www, andstaff. - The
admingroup grants sudo privileges, similar to Linux’ssudogroup. - Apple’s Mobile Device Management (MDM) solutions extend group policies to fleets of devices.
For developers and system administrators, understanding macOS’s dual nature—Unix foundation with GUI abstraction—is key to effective system group management.
System Group in Network and Cloud Infrastructure
As organizations move toward distributed computing and cloud-native architectures, the role of the system group expands beyond individual machines to encompass entire networks, virtual machines, containers, and microservices. In this context, system groups become dynamic, policy-driven entities rather than static user lists.
Group Management in Enterprise Networks
In large enterprise networks, managing access manually is impractical. Centralized identity management systems like LDAP (Lightweight Directory Access Protocol) or Microsoft Active Directory serve as the backbone for defining and enforcing system group policies.
- LDAP organizes users and groups in a hierarchical directory tree.
- Groups can be nested, allowing for complex permission structures (e.g.,
IT-Adminsinherits fromEmployees). - Single Sign-On (SSO) systems leverage group membership to grant access to multiple applications.
Tools like OpenLDAP and Keycloak provide open-source solutions for scalable group management.
Cloud Platforms and Identity Federation
Major cloud providers—Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP)—have redefined what a system group means in a virtualized world. Here, groups are part of Identity and Access Management (IAM) frameworks.
- In AWS, IAM Groups allow administrators to attach policies to multiple users at once.
- Azure uses Microsoft Entra ID (formerly Azure AD) to manage security groups across cloud resources.
- GCP employs Cloud Identity to define groups with granular permissions.
These cloud-based system groups support conditional access, multi-factor authentication, and real-time auditing—features that were once impossible in traditional on-premise setups.
Containerization and Orchestration: Docker and Kubernetes
In containerized environments, system groups take on new significance. For example, Docker allows users to be added to the docker group to run containers without root privileges. However, this can be a security risk if not properly managed, as Docker daemons have near-root capabilities.
- The
dockergroup effectively grants elevated system access. - Kubernetes uses Role-Based Access Control (RBAC) with
ClusterRolesandRolesto define permissions for users and service accounts. - Namespaces in Kubernetes can be associated with logical groups for resource isolation.
Best practices recommend minimizing membership in privileged groups and using tools like Pod Security Policies (now deprecated) or Gatekeeper for policy enforcement.
System Group in Software Development and DevOps
Modern software development relies heavily on automation, collaboration, and secure access control—all areas where the concept of a system group plays a pivotal role. From version control systems to CI/CD pipelines, group-based permissions ensure that the right people have the right access at the right time.
Version Control Systems: GitHub, GitLab, and Bitbucket
In platforms like GitHub and GitLab, system groups manifest as teams or organizations. These virtual groups map to real-world teams and control access to repositories, issues, and deployment environments.
- GitHub Teams allow administrators to assign roles (read, write, admin) to groups of users.
- GitLab uses groups as top-level containers for projects, subgroups, and CI/CD configurations.
- Access to protected branches can be restricted to specific system groups.
For example, only members of the devops-engineers group might be allowed to merge into the main branch or deploy to production. Learn more about GitLab group management at GitLab Official Docs.
CI/CD Pipelines and Role-Based Access
Continuous Integration and Continuous Deployment (CI/CD) pipelines are secured using system group principles. Tools like Jenkins, CircleCI, and GitHub Actions use group-based permissions to control who can trigger builds, view logs, or approve deployments.
- Jenkins uses Matrix-based Security or Role-Based Strategy plugins to assign permissions by group.
- GitHub Actions allows workflows to require approval from users in specific teams (groups).
- Azure DevOps uses Security Groups to manage access across pipelines, repositories, and work items.
This ensures that sensitive operations—like deploying to production—are only accessible to authorized personnel, reducing the risk of accidental or malicious changes.
Service Accounts and Machine Identities
Beyond human users, system groups also include service accounts—non-human identities used by applications, scripts, or machines. These are often grouped logically (e.g., web-servers, database-clients) to apply consistent policies.
- Service accounts can be members of system groups to inherit permissions.
- In Kubernetes,
ServiceAccountobjects are bound toRolesviaRoleBindings, mimicking group-based access. - Best practice: Rotate credentials and limit privileges for service accounts.
As automation increases, managing machine identities through system groups becomes as important as managing human access.
System Group Policies and Governance
Effective governance of system groups is essential for maintaining security, compliance, and operational efficiency. Without proper policies, group membership can become chaotic, leading to “group sprawl” and excessive privileges.
Principles of Least Privilege and Role-Based Access
The principle of least privilege dictates that users and processes should only have the minimum access necessary to perform their tasks. System groups are a primary tool for enforcing this principle.
- Create groups based on job functions (e.g.,
finance-analysts,network-admins). - Avoid broad groups like
everyoneorall-userswith high privileges. - Regularly audit group memberships to remove inactive or unauthorized users.
Role-Based Access Control (RBAC) formalizes this approach, making system groups a cornerstone of enterprise security frameworks.
Audit and Compliance Requirements
Regulatory standards such as HIPAA, SOX, and GDPR require organizations to maintain detailed records of who has access to what data. System groups simplify compliance by providing a structured way to document and review access rights.
- Generate regular reports of group memberships and permissions.
- Implement automated alerts for changes to critical groups (e.g.,
sudoordomain-admins). - Use tools like OSSEC or Wazuh for real-time monitoring of group changes.
For example, under GDPR, data processors must demonstrate accountability—system group audits help prove that access is properly controlled.
Automating Group Lifecycle Management
Manual group management doesn’t scale. Automation tools like Ansible, Puppet, and Terraform can define, deploy, and maintain system groups across hundreds or thousands of systems.
- Ansible playbooks can ensure consistent group configuration across servers.
- Puppet uses manifests to declare group states and enforce them.
- Terraform can provision IAM groups in cloud environments as code.
Infrastructure as Code (IaC) transforms system group management from an ad-hoc task into a repeatable, version-controlled process.
Common Challenges and Best Practices for System Group Management
While system groups offer powerful benefits, they also introduce challenges—especially in large or hybrid environments. Misconfigurations, outdated memberships, and privilege creep can undermine security and performance.
Privilege Escalation Risks
One of the most serious risks is unintended privilege escalation. For example, adding a user to the docker group on Linux can allow them to gain root access by mounting the host filesystem into a container.
- Always assess the implied privileges of a group before adding users.
- Use tools like
auditdto monitor group-related system calls. - Consider using user namespaces in Docker to mitigate risks.
Security teams should treat group membership reviews with the same rigor as password policies.
Group Sprawl and Orphaned Memberships
Over time, organizations accumulate unused or redundant groups—often due to employee turnover or project closures. This “group sprawl” makes audits difficult and increases attack surface.
- Implement a group lifecycle policy: define creation, review, and deletion procedures.
- Use naming conventions (e.g.,
proj-xyz-dev) to make group purposes clear. - Automate cleanup of inactive groups using scripts or IAM tools.
Regular cleanups should be part of routine system maintenance.
Best Practices Summary
To maximize the benefits of system groups while minimizing risks, follow these best practices:
- Use descriptive names for groups (e.g.,
db-backup-operatorsinstead ofgroup1). - Limit nested groups to avoid complexity and permission conflicts.
- Enforce multi-factor authentication for membership in privileged groups.
- Document group purposes and maintain an access control matrix.
- Train administrators on secure group management practices.
“The strength of your system’s security is only as strong as your weakest group permission.” — Cybersecurity Best Practices Guide, NIST
Future Trends: AI, Zero Trust, and Decentralized Identity
The concept of a system group is evolving in response to new technologies and security paradigms. As organizations adopt AI-driven operations, Zero Trust architectures, and decentralized identity models, the way we define and manage groups is undergoing a fundamental shift.
AI-Powered Access Management
Artificial Intelligence is beginning to play a role in predicting and automating group membership. Machine learning models can analyze user behavior to suggest appropriate group assignments or flag anomalies.
- AI can detect when a user is performing actions outside their normal group-based role.
- Predictive analytics can recommend group changes during onboarding or role transitions.
- Tools like Microsoft’s Identity Protection use AI to assess risk based on group activity.
This proactive approach enhances security while reducing administrative burden.
Zero Trust and Dynamic Grouping
The Zero Trust security model assumes no user or device should be trusted by default—even if they’re inside the network. In this model, system groups are no longer static; they become dynamic, context-aware entities.
- Access is granted based on real-time factors: location, device health, time of day.
- Groups may be temporary and session-based rather than permanent.
- Google’s BeyondCorp model exemplifies this shift, where access is determined by identity and context, not network position.
System groups in a Zero Trust environment are fluid, policy-driven, and continuously verified.
Decentralized Identity and Blockchain-Based Groups
Emerging technologies like blockchain and decentralized identifiers (DIDs) are paving the way for self-sovereign identity. In this model, users control their own identities, and system groups could be formed through cryptographic proofs rather than centralized directories.
- Smart contracts could define group membership rules on a blockchain.
- Verifiable credentials allow users to prove group affiliation without revealing unnecessary data.
- Projects like Microsoft ION and Hyperledger Aries are exploring decentralized identity frameworks.
While still in early stages, this could revolutionize how system groups are managed across organizations and borders.
What is a system group?
A system group is a logical collection of users, processes, or devices that share common access rights or roles within a computing environment. It is used to manage permissions and simplify administration in operating systems, networks, and cloud platforms.
How do system groups improve security?
System groups enhance security by enabling role-based access control, enforcing the principle of least privilege, and allowing centralized management of permissions. They reduce the risk of unauthorized access and simplify auditing and compliance.
What is the difference between a system group and a user group?
A system group is typically reserved for system-level processes and services (e.g., daemon, sys), while a user group is created for human users to manage file and resource access. System groups often have lower GIDs and are critical for OS functionality.
How are system groups used in cloud environments?
In cloud platforms like AWS, Azure, and GCP, system groups are implemented through IAM (Identity and Access Management) services. IAM groups allow administrators to assign policies to multiple users, enabling scalable and secure access control across cloud resources.
Can system groups be automated?
Yes, system groups can be automated using tools like Ansible, Puppet, Terraform, and cloud-native IAM APIs. Automation ensures consistency, reduces human error, and supports Infrastructure as Code (IaC) practices.
Understanding the system group is no longer optional—it’s a fundamental skill for IT professionals, developers, and security experts. From local user management to global cloud infrastructures, system groups provide the structure needed to control access, enforce policies, and maintain security. As technology evolves, so too will the ways we define and use these groups, moving toward dynamic, intelligent, and decentralized models. By mastering the principles outlined in this guide, you’ll be well-equipped to navigate the present and future of system group management.
Further Reading: